Modern browser privacy controls reduce invasive tracking, but they also shorten the lifetime of legitimate, consented first‑party cookies in Safari, sometimes purging them after about a week of inactivity. This causes repeat consent prompts and breaks returning‑user recognition. See Tracking Prevention in WebKit for details.
This is annoying and costly, but it’s especially important in opt‑out models like California’s CCPA, where site owners may be required to honor opt‑outs for extended periods and avoid unnecessary re‑prompting. If Safari removes the consent cookie because a user didn’t revisit in a given time window, you risk resuming tracking until they opt out again, an audit risk created by well‑intended built-in browser behavior. Even opt-in models like the GDPR require that you hang onto consent decisions and don’t keep prompting, but that’s only possible if you’re able to retain the relevant cookies.
The right fix is to preserve the decision in a controlled, first‑party place that isn’t governed by the same browser lifetime rules.
Why a first‑party reverse proxy is the right lever
At a high level, a proxy server acts as an intermediary for requests from clients seeking resources from other servers. Instead of connecting directly, the client connects to the proxy, which then forwards the request to the target server.
That means the proxy ensures that browsers talk to your domain first – a first-party reverse proxy can receive first-party requests from the browser, then forwards to Tealium services (and other trusted vendors) behind the scenes. That single shift unlocks durable cookie handling and governance, because the browser doesn’t see the third-party servers working behind the scenes, unlocking durable cookies and governance opportunities.
The pattern is as first‑party as it gets: run on your own domain and edge. It effectively negates any first-party features vendors deliver and shifts control to the site owner, with impressive long‑term benefits even though it requires build‑and‑maintain efforts.
- Durable consent and identity. Store server‑side copies of specific cookies and restore them client‑side only when appropriate. This mitigates first‑party lifetime limits (like Safari’s ITP) while respecting consent flows.
- Granular governance. Decide exactly which cookies to persist, for how long, and with what attributes. Remove or rewrite cookies (even HttpOnly cookies) that are set by proxied servers.
- First‑party routing for trusted services. Forward Tealium iQ, Tealium Collect, and Data Layer Enrichment (DLE) through your domain, which reduces exposure to browser limitations and some list‑based blocking patterns that key on subdomain.
- Additional ad‑block hardening options. Optionally rewrite browser‑visible paths to remove strings like “utag” and then restore them post-proxy so vendor origins still receive standard paths that the browser never sees, helping with even the most restrictive Adblock tools.
- Performance, control, and resilience. The edge is close to users and under your control. You can add small, targeted behaviors without waiting on vendor releases or incurring extra round trips. We easily added IP addresses into Tealium Collect payloads – the pattern gives you a flexible, first-party way to really control how your users are tracked and your cookies are persisted.
How it works
Generally, this is how a website looks, though this is an over-simplified example – most modern sites have quite a few more sources of content than this.
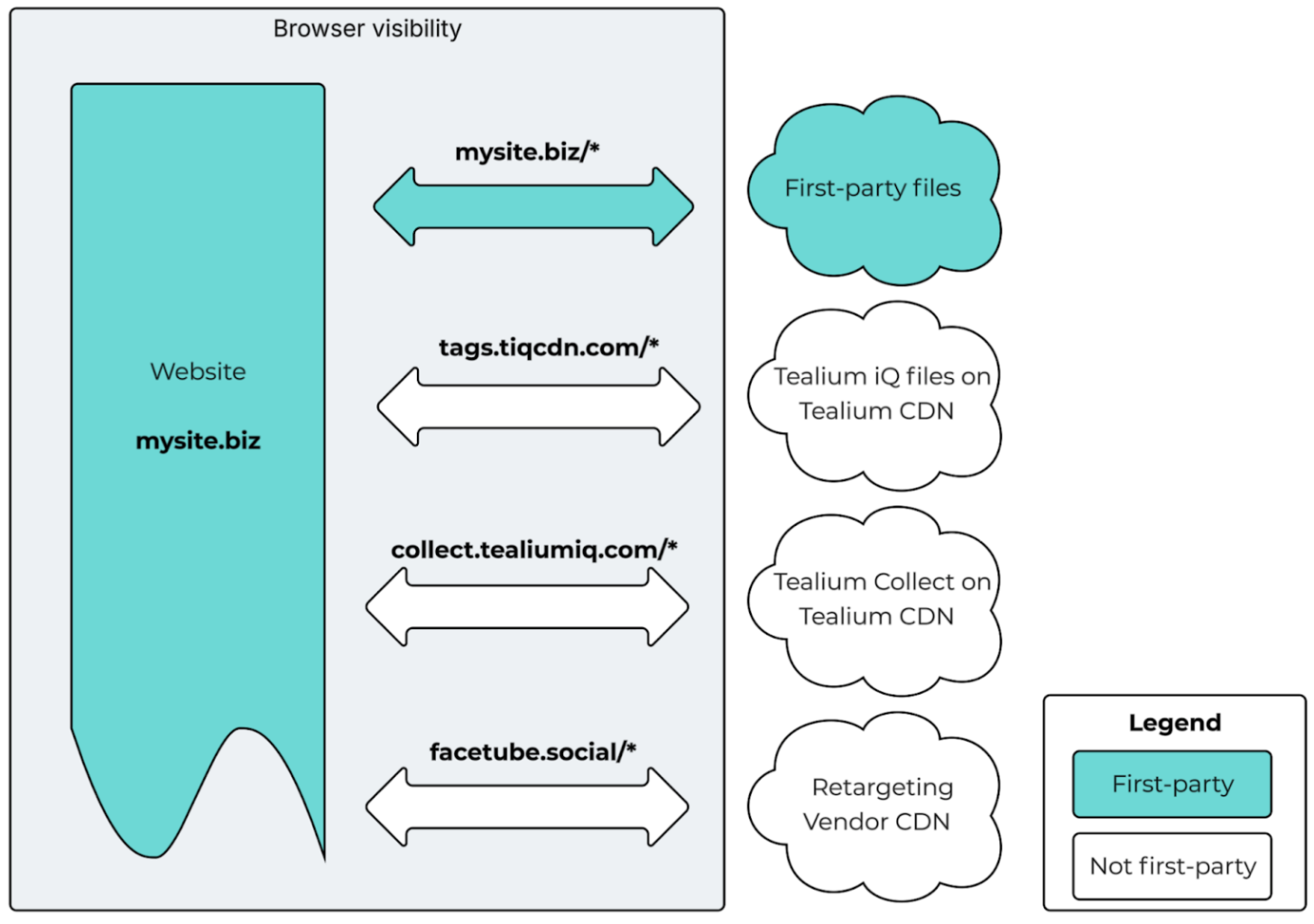
Above, the only first-party files are the ones that come from the customer’s own CDN – this is standard.
Adding a first-party reverse proxy lets a site owner use a set of first-party paths to act as a middleman between the browser and the third-party CDNs.
With a reverse proxy, a first-party path (from the browser’s perspective) can load a file that’s hosted by a third party, with the ability to edit both the request and response as needed, without DNS or certificate updates.
Below, mysite.biz/fwd-teal-cdn/* will forward the requests and responses from the tags.tiqcdn.com/*, where * is any path on that subdomain (modifying request and response as appropriate).
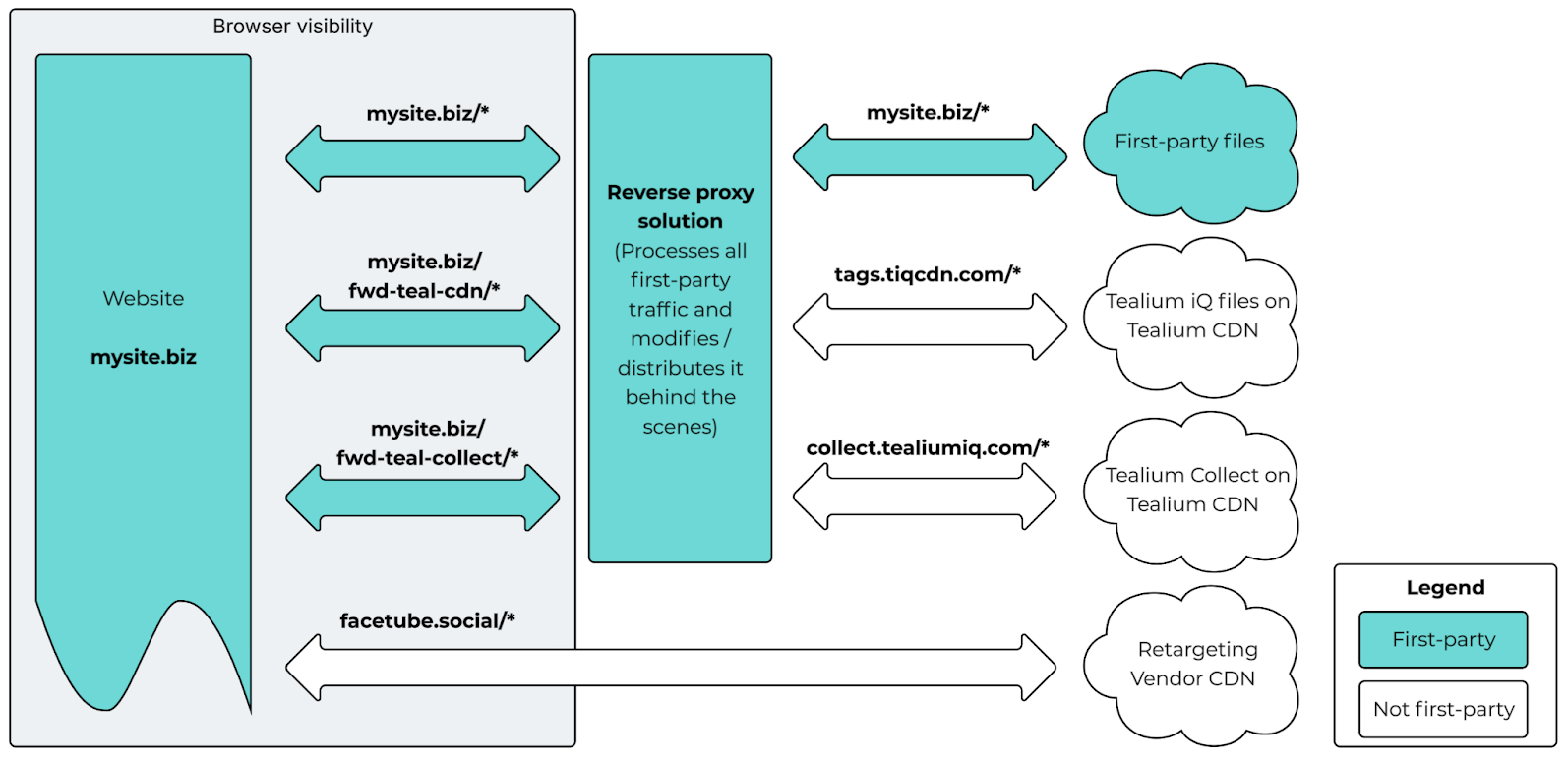
That powerful approach allows you to make first-party requests to third party servers without each vendor needing to add features (or even know it’s happening). It also allows the requests and responses to be edited as needed.
It also makes very useful patterns more accessible, like setting first-party http-only copies of critical cookies (this type of cookie isn’t removed by Safari). Those cookies can be restored into client-side readable versions with each request, allowing you to preserve consent and identity beyond what Safari allows for client-side persistence, improving analytics, returning visitor recognition, attribution, consent decisions and more.
It also makes those requests first-party from the perspective of browser and adblocks by obfuscating the final URLs behind the reverse proxy, which can include any number of path rewrites as needed.
Should everything run through my shiny new reverse proxy?
No, actually – you’ll notice that we left facetube.social requests third-party in the diagrams above. That’s because that imaginary social site relies on third-party cookies to work correctly, which makes it incompatible with first-party tracking strategies (because third-party cookies rely on third-party requests).
(Much) more detail in the next post
This is the first in a set of posts – we will be publishing the full details of a working implementation of this kind of reverse proxy solution using Cloudflare Workers here: (Build first‑party durability with Cloudflare Workers).




